Cybersecurity frameworks implementation ape targeting specific
Are you concerned about cybersecurity and how it affects your business? You're not alone! In today's digital age, cyber threats are a constant worry for organizations big and small. Luckily, there are frameworks and strategies available to help protect your valuable data. Let's dive into the world of cybersecurity frameworks, their types, strategies, and implementation, and find out how they can safeguard your business.
Cybersecurity Frameworks - Types and Importance
When it comes to cybersecurity frameworks, there are various types to choose from. These frameworks provide a set of guidelines and best practices to strengthen the security posture of your organization. One popular framework is the NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology.
Implementing the NIST Cybersecurity Framework

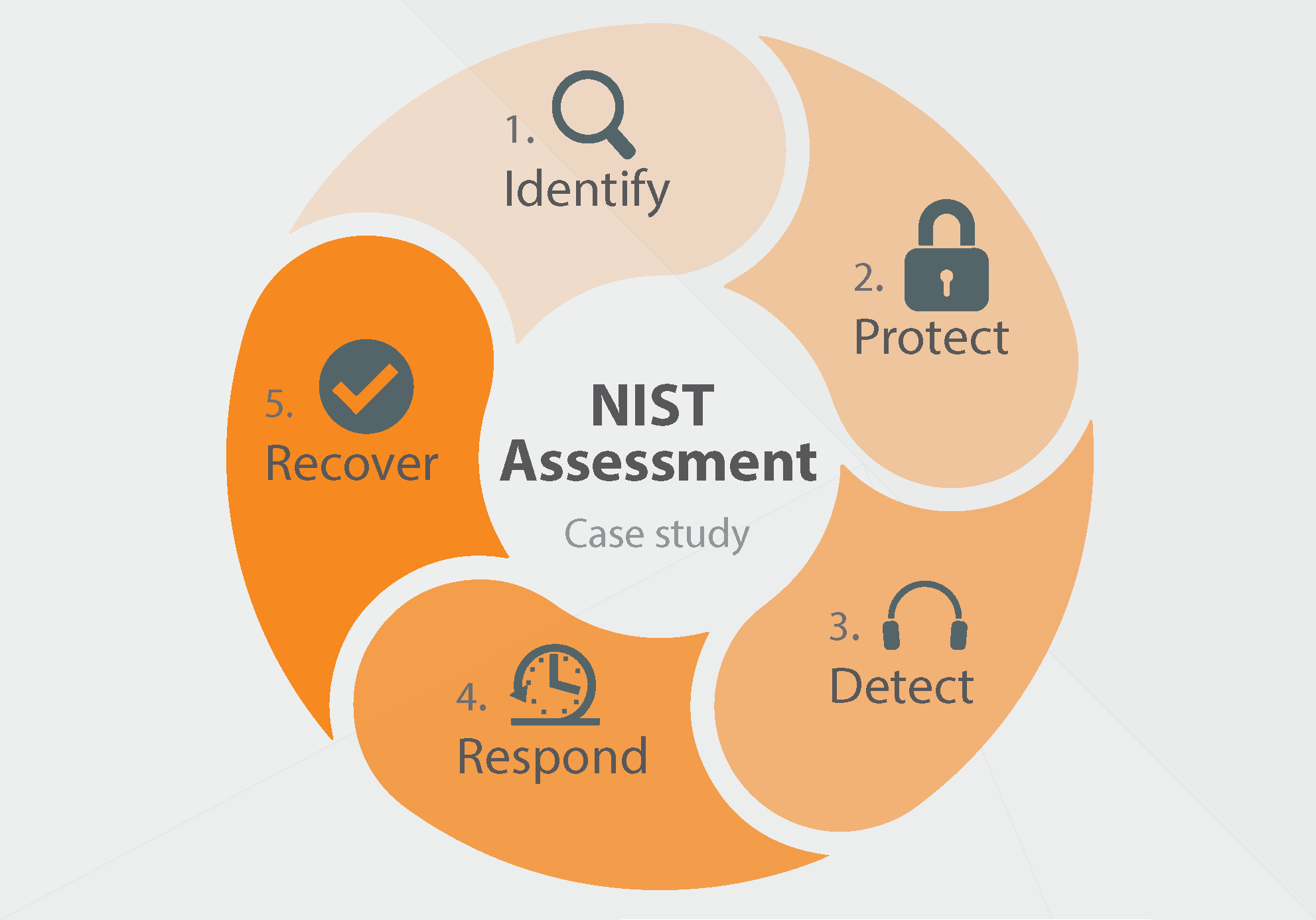
The NIST Cybersecurity Framework is widely recognized and provides a structured approach to managing and mitigating cyber risks. By implementing this framework, you can effectively identify, protect, detect, respond to, and recover from cyber threats.
When it comes to implementing the NIST Cybersecurity Framework, there are several steps to consider:
Step 1: Prioritize and Assess Risks
Start by identifying the critical assets and systems in your organization. Conduct a thorough risk assessment to understand potential vulnerabilities and the impact of a successful cyber attack.
Step 2: Establish Policies and Procedures
Create comprehensive cybersecurity policies and procedures that align with the NIST Framework. These should cover areas such as access control, incident response, data encryption, and employee training.
Step 3: Implement Security Controls
Based on the identified risks, implement appropriate security controls to protect your systems and data. This may include firewalls, antivirus software, multi-factor authentication, and encryption.
Step 4: Monitor and Detect Threats
Regularly monitor your systems for any suspicious activity or potential threats. Implement intrusion detection systems and conduct vulnerability assessments to ensure early detection.
Step 5: Respond and Recover
In the unfortunate event of a cyber attack, have an incident response plan in place to contain the breach, minimize damage, and restore systems to normal operations as quickly as possible. Learn from the incident and update your security measures accordingly.
Step 6: Continuous Improvement
Cybersecurity is an ongoing process. Regularly review and update your policies, procedures, and controls to address new risks and technologies. Stay informed about the latest cyber threats and educate your employees about security best practices.
Implementing the NIST Cybersecurity Framework can significantly strengthen your organization's defense against cyber threats. By following these steps, you'll be well-prepared to safeguard your valuable data and protect your business.
Remember, cybersecurity is a constant battle, and staying ahead of cybercriminals requires a proactive approach. By adopting the right frameworks and implementing robust security measures, you can create a secure environment for your organization's digital assets.