Cybersecurity policy characteristics successful
A successful cybersecurity policy is essential in today's digital world. It provides guidelines and measures to protect your organization's sensitive information from potential threats. In this post, we will discuss the seven characteristics of a successful cybersecurity policy and when it is time to update it.
1. Clear and Comprehensive:
A successful cybersecurity policy should clearly outline all the rules, regulations, and best practices that employees need to follow. It should cover all aspects of cybersecurity, including password management, network security, data encryption, and incident response procedures.

Image Source: Kelser Corporation
2. Regularly Updated:
Cyber threats are continuously evolving, and so should your cybersecurity policy. It is important to stay updated with the latest industry practices and emerging threats. Regularly review and update your policy to address new vulnerabilities and strengthen your defenses.
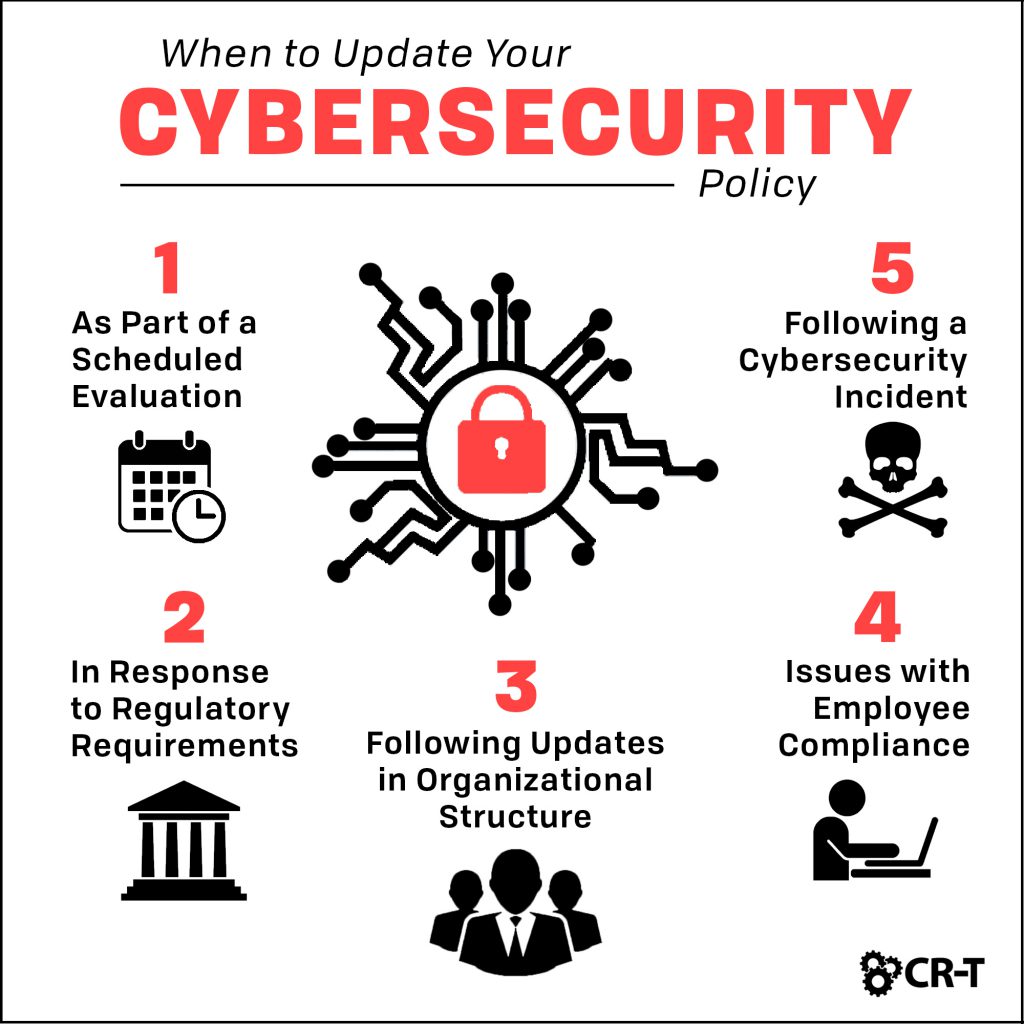
Image Source: CR-T
3. Employee Awareness and Training:
Employees are often the weakest link in cybersecurity. A successful policy should include provisions for regular training and awareness programs to educate employees about potential cyber threats and how to prevent them. This can significantly reduce the risk of human error leading to security breaches.
4. Compliance with Regulations:
A successful cybersecurity policy should ensure compliance with relevant regulations and industry standards. This includes understanding and implementing measures required by laws such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
5. Access Control:
Access control is crucial in protecting sensitive information from unauthorized access. A successful policy should include measures to restrict access to confidential data based on the principle of least privilege. This ensures that only authorized personnel can access sensitive information.
6. Incident Response Plan:
No matter how robust your cybersecurity measures are, there is always a possibility of a security incident. A successful policy should have a well-defined incident response plan that outlines the steps to be taken in case of a data breach or any other cyber incident. This helps in minimizing damage, containing the incident, and recovering quickly.
7. Regular Security Audits:
Evaluating the effectiveness of your cybersecurity policy is crucial. Regular security audits should be conducted to identify any weaknesses or vulnerabilities in your systems and policies. These audits help in assessing the overall security posture of your organization and provide valuable insights for improvement.
In conclusion, a successful cybersecurity policy is the foundation of effective cybersecurity practices. By ensuring a clear and comprehensive policy, regular updates, employee awareness and training, compliance with regulations, access control measures, incident response plans, and regular security audits, your organization can significantly strengthen its defenses against cyber threats.
Remember, cybersecurity is an ongoing process, and it is essential to stay informed and adapt to the evolving threat landscape.